How Amazon Uses Privacy-Enhancing Technologies (PETs) in AdTech

Amazon’s commitment to data privacy is evident in their adoption of privacy-enhancing technologies (PETs) into technical processes and company-wide policies.
The company employs these technologies across their products, including AWS Data Protection Services, Amazon Security Lake, AWS Clean Rooms, and privacy features in Alexa and Echo.
This article explains how Amazon safeguards customer data throughout their various processes and privacy-enhancing technologies.
This is also the fifth entry in our series of articles on tech giants adopting PETs.
Key Points
-
Amazon prioritises customer data protection and employs PETs across their services.
-
AWS Data Protection Services offer encryption, tokenisation, access control, and more to enhance data privacy.
-
Amazon’s shared-responsibility model ensures both AWS and the clients play roles in cloud security.
-
AWS provides security services in six categories: identity and access management, detection, network and application protection, data protection, incident response, and compliance.
-
Amazon Security Lake centralises security data and allows integration with various sources.
-
AWS Clean Rooms facilitate secure data analysis and collaboration.
-
Amazon places a strong emphasis on user privacy with Alexa and Echo.
-
Privacy-enhancing technologies in Alexa include tokenisation, data minimisation, and encryption.
How Is Amazon Adopting Privacy-Enhancing Technologies?
Amazon is fully focused on customer needs, and one aspect of this is to ensure customer data is protected through the entire processes of ingestion, transportation, storage, processing, and modelling.
For every system managing customer data, Amazon’s policies specify things like:
-
The cryptographic requirements that must be met
-
Authentication procedures
-
Policy compliance monitoring processes through the entire lifecycle of the system or service
AWS Data Protection Services
Amazon Web Services defines data as “the most critical and sensitive customer assets” and provides various processes, services, and tools that enhance privacy.
For instance, the Security Pillar of the AWS Well-Architected Framework is a guideline that helps users build reliable, secure, efficient, and cost-effective systems on AWS.
Among the framework’s design principles, AWS lists the following privacy-enhancing technologies they provide along with their services:
-
Encryption
-
Tokenisation
-
Access control, e.g. multi-factor authentication
-
Cryptography
-
Post-quantum cryptography
-
Automated reasoning technology
-
Zero Trust guiding principles
Additionally, Amazon believes in a shared-responsibility model, where AWS is responsible for the security of the cloud, and the client is responsible for the security in the cloud.
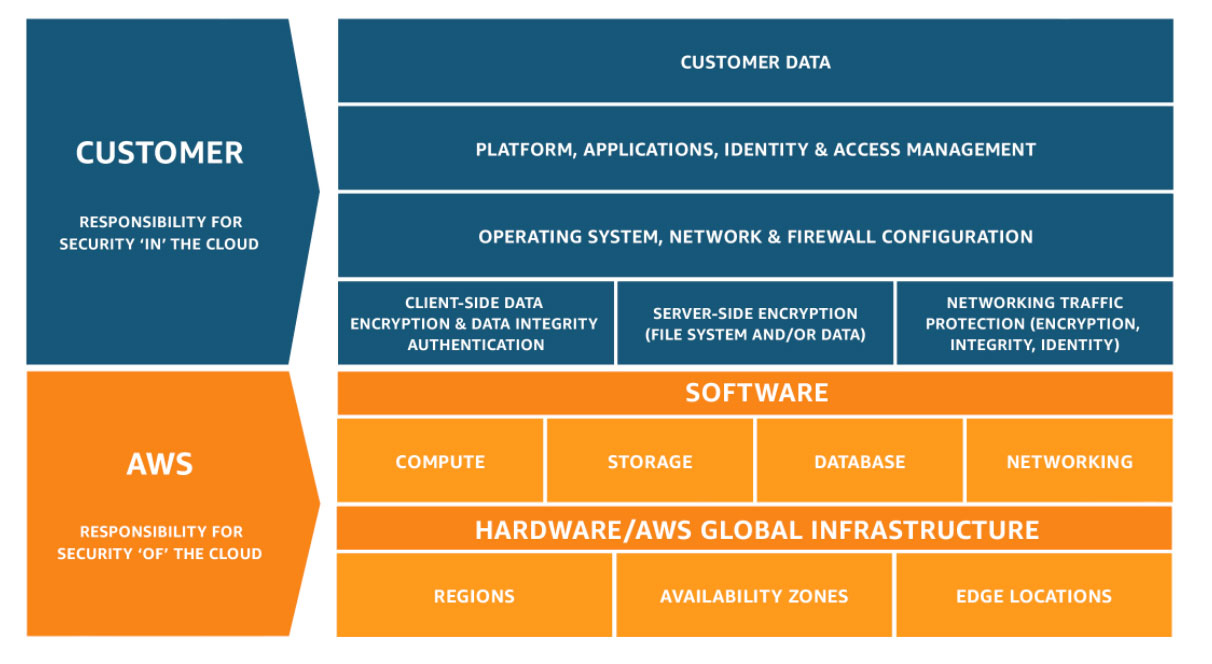
Shared-responsibility model by AWS. Source: AWS Amazon.
Amazon created a number of security services to protect data and help users handle data privacy. The company divides these services into six categories: identity and access management, detection, network and application protection, data protection, incident response, and compliance.
Here are some examples of the services from each category:
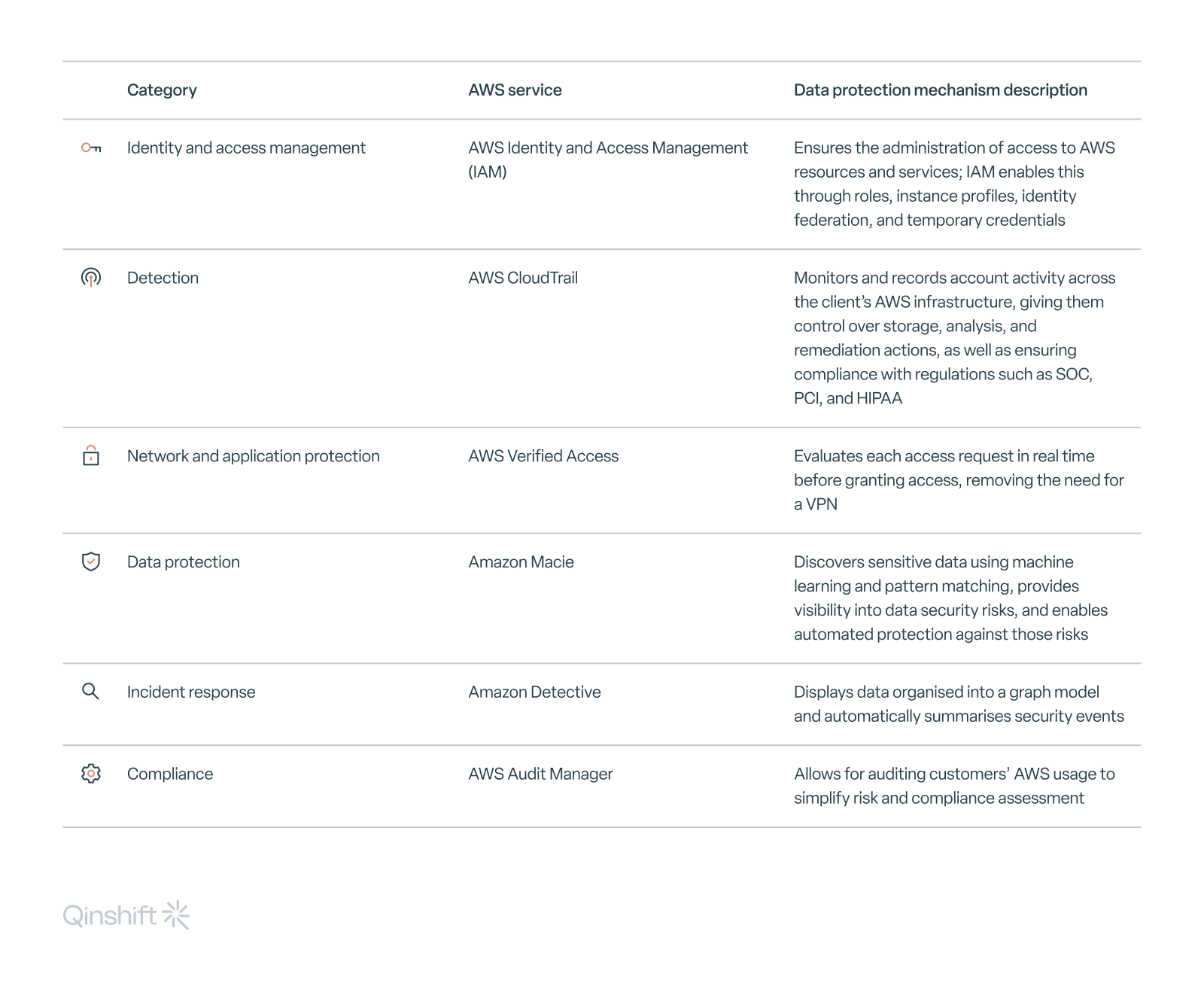
In addition to this division, AWS also created:
-
AWS CloudHSM and AWS Key Management Service to facilitate the secure creation and management of encryption keys,
-
AWS Control Tower to manage data residency and control,
-
AWS Encryption SDK to implement encryption and decryption operations on all types of data.
Clearcode, part of Qinshift, used AWS encryption libraries to deliver privacy-compliant projects to their clients:
-
AdOps Reporting Dashboard — Clearcode used AWS S3, an object storage service that delivers its buckets private by default, with access granting being done via the access management feature. In this project, the client’s challenge was to compute and aggregate the metrics, then display them on the reporting dashboard.
-
SITO — Clearcode utilised a mix of AWS, including DynamoDB Encryption Client, a client-side library for encrypting data tables, before sending it to a database for a mobile DSP that helps the world’s largest brands reach their audiences via location-based technology.
Amazon Security Lake
In 2023, AWS announced the general availability of Amazon Security Lake — a service designed to help organisations centralise their security data from various sources, including AWS environments, SaaS providers, on-premises setups, and other cloud sources.
The Security Lake converts incoming security data into the Open Cybersecurity Schema Framework (OCSF) open standard, enabling security teams to work with consistent and normalised data, simplifying investigations and analysis.
Amazon Security Lake enables security teams to collect, combine, and analyse security data from over 80 sources, including AWS, security partners, and analytics providers. This provides a unified view of an organisation’s security posture, enhancing the ability to detect, investigate, and respond to potential security threats.
So far, Cribl, CrowdStrike, Datadog, SentinelOne, Splunk, Wiz, and more than 50 other companies have integrated their technologies with Amazon Security Lake.
AWS Clean Rooms
AWS Clean Rooms facilitates streamlined and secure analysis and collaboration between organisations and their partners, so that the companies can generate insights from advertising campaigns, investment strategies, as well as research and development endeavours.
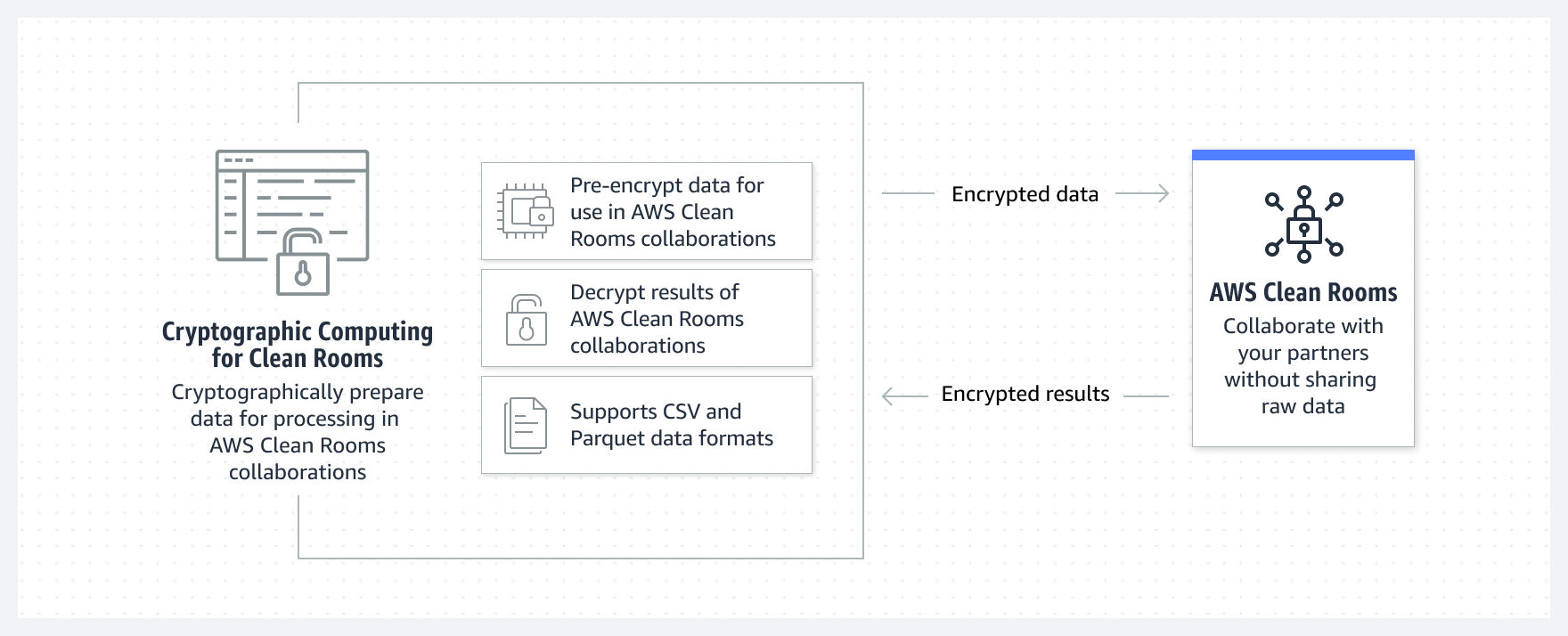
Cryptographic Computing for Clean Rooms. Source: AWS Amazon
AWS Clean Rooms helps protect data in several ways:
-
Analysis rules
AWS Clean Rooms allows users to set up analysis rules that limit the types of queries that can be run on the data tables. Rules can be defined for aggregation, list, and custom analyses.
-
Column controls
For aggregation and list analysis rules, the user can control how each column of the data can be used in queries. This prevents unauthorised filtering, joining, or aggregating of data columns.
-
Encryption during collaboration
AWS Clean Rooms offers Cryptographic Computing for Clean Rooms (C3R), which lets users pre-encrypt data using a shared secret key. This encryption remains active during the collaboration.
-
Direct S3 access
AWS Clean Rooms reads data directly from the user’s designated Amazon S3 location for analysis. This eliminates the need to store data within clean rooms and reduces the exposure of sensitive data.
-
Compliance with data privacy laws
AWS Clean Rooms provides granular control over data sharing, enabling compliance with data privacy laws.
-
HIPAA eligibility
Amazon’s product is HIPAA eligible, which means it meets the standards for handling sensitive health care data.
Alexa and Echo
Amazon created their own voice assistant called Alexa. More specifically, Alexa is a speech recognition system and a mobile application, while Echo is the name of the input and output devices for Alexa.
The pair is equipped with multiple layers of privacy protection and controls to deliver an undisrupted user experience with daily activities.

Alexa Home Screen displays static full-screen ads on Echo devices. Advertisers can display their content in rotation with weather, recipes, sports, and news, while the customer can interact with the ads using voice commands and tapping on the screen.
Inside the Echo device is a microphone and an acoustic pattern in a loop responsible for waking the system up with the wake word, i.e. the device includes an on-device keyword spotting mechanism. If the wake word was detected — and only then — Echo streams the voice command to Alexa Cloud.
For example, if a customer wants to watch a video commercial, they would simply say, “Alexa, play video”, whereas going to a detailed product page would be called out by saying, “Alexa, show more”.
The Alexa system consists of services processing requests in Alexa Cloud: Automatic Speech Recognition (ASR), Natural Language Understanding (NLU), Text to Speech (TTS), and Alexa Data Store. The system utilises external data sources if needed, but only when agreed upon by the user.
Privacy-enhancing technologies used in the Alexa system and Echo devices include the following solutions:
-
The customer’s personal information (e.g. name or address) is not released to the third party unless specifically requested to be shared by the customer. Amazon’s permission framework helps customers manage their permissions to share data.
-
Third parties receive a token instead of the customer’s Amazon account identifiers.
-
With cloud-side verification, Alexa double-checks to ensure that the wake word was really spoken.
-
Amazon stores data collected by Alexa in various services such as S3 and DynamoDB, each with associated retention and access policies.
-
Amazon strives to minimise the amount of data retained.
-
Only individuals with an approved need and appropriate permissions are granted access to specific data. Access permissions are periodically reviewed, and access to sensitive data is audited.
-
Sensitive customer data, including voice recordings, is stored in encrypted form, both at rest and during transit.
-
System-level data is stored in log files for troubleshooting and security incident resolution purposes. These logs are encrypted, and access is restricted to authorised teams. They don’t contain customer voice recordings or data derived from such recordings.

