How Google Uses Privacy-Enhancing Technologies (PETs) in AdTech

Google, one of the most important companies in the AdTech world, stands at the forefront of developing and adopting privacy-enhancing technologies (PETs), i.e. technologies that secure user data from misuse.
Despite criticism of Google’s use of user data for advertising, the tech giant has implemented measures to protect the gathered and retained user data.
In this article, you’ll learn:
-
What privacy-enhancing technologies does Google use?
-
How does Google adapt PETs into its AdTech stack?
-
How does Google collaborate with other AdTech giants to provide the most secure standards?
First, let’s look at how Google applies PETs in professional and individual environments, then we’ll explore the A
Key Points
-
Google adopted privacy-enhancing technologies like federated learning, differential privacy, and fully homomorphic encryption to protect and minimise personal data usage.
-
Google’s Privacy Sandbox initiative for the open web and Android aims to give users more control over their privacy settings while offering advertisers tools to measure ad effectiveness.
-
Google transitioned from Federated Learning of Cohorts (FLoC) to Topics API and Protected Audience API to ensure the use of user interests for ad targeting without revealing individual data.
Privacy-Enhancing Technologies Used by Google
Google designs their products with a privacy-centric approach in mind. The company uses existing and new privacy-enhancing technologies to create a safer Internet.
For instance, the company applied a zero-trust approach to Google Workspace by customising management access for enterprise use, building features for securing data, and incorporating encryption and endpoint protection.
Another example is 2-Step Verification (2SV), which secures Google Accounts. Along with Apple and Microsoft, Google wants to expand the adoption of a common passwordless sign-in standard developed by the FIDO Alliance and the World Wide Web Consortium.
Lastly, when a user enters payment details at an online checkout, the autofill function in virtual cards replaces the actual card number with a distinct virtual number in real time.
Protected Computing
Looking strictly at technologies and not products, Google contributed to developing federated learning (FL), differential privacy (DP), and fully homomorphic encryption (FHE) to minimise and protect personal data usage.
On top of these PETs, the giant from Silicon Valley is now building Protected Computing, a set of tools for enhancing privacy. The company focuses on cloud enclaves, edge processing, and end-to-end encryption.
Below, you’ll find implementations of various PETs under Protected Computing:
-
Android’s Private Compute Core establishes a secure space isolated from the operating system and other applications.
-
Google’s Virtual Private Network (VPN) secures network traffic by masking the IP address.
-
Android Backup ensures that your stored data remains encrypted end-to-end, maintaining security even when kept in cloud storage.
Privacy Sandbox
Google’s initiative for running key programmatic advertising processes for the web and in-app mobile advertising called the Privacy Sandbox is a set of proposed technologies for privacy enhancements within the Chrome browser and Android operating system.
The main objective of the Privacy Sandbox is to hand off control over privacy settings to users. At the same time, it gives advertisers tools to reach their target audience and measure the effectiveness of their targeted and personalised ads.
Each proposal within the Privacy Sandbox fulfils one of the functions associated with programmatic advertising, which third-party cookies currently carry.
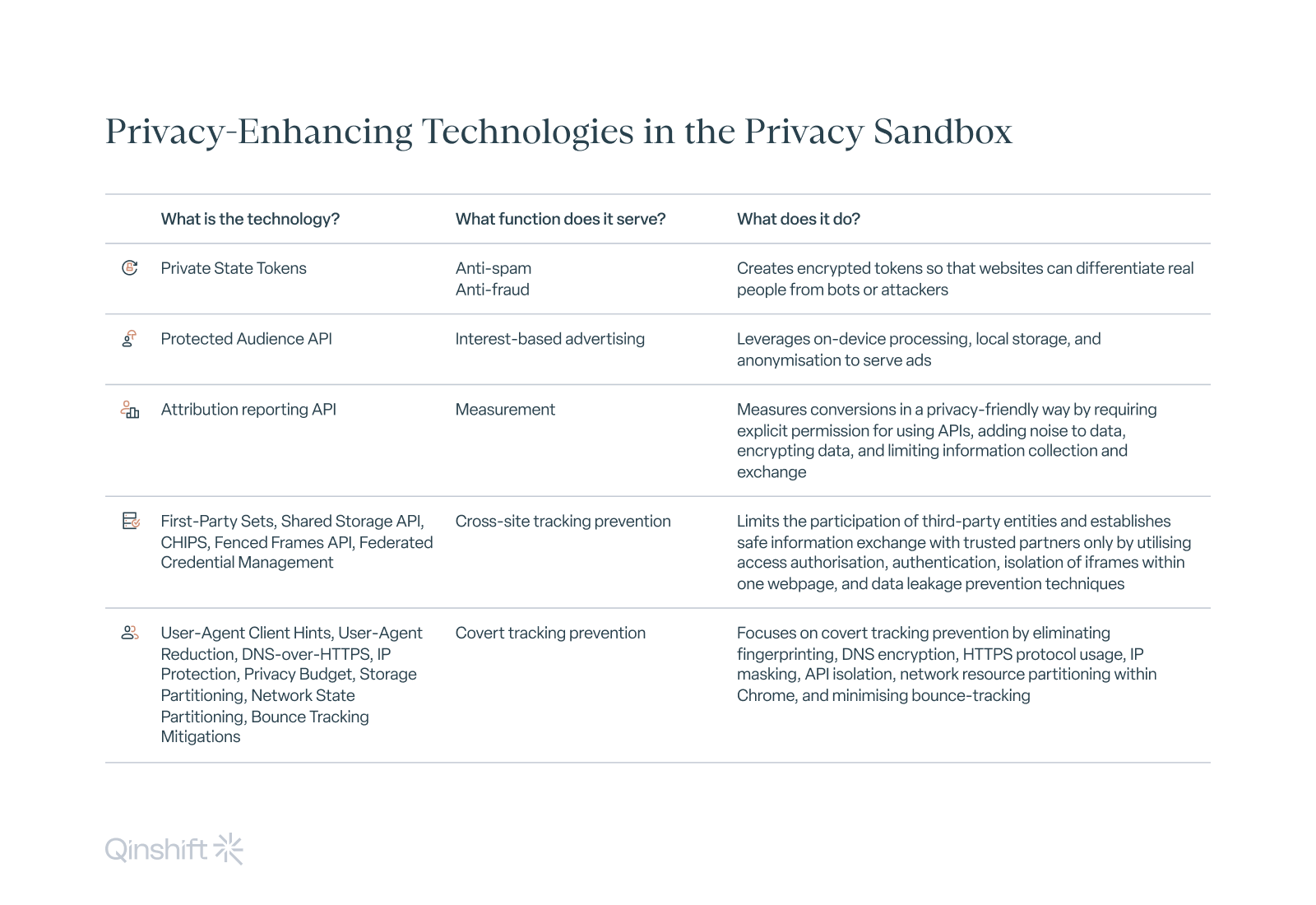
Anti-spam and anti-fraud: Private state tokens
Private state tokens help websites differentiate real people from bots or attackers.
When a user visits a site regularly, e.g. by logging into their account, the site can give their browser a private state token. Other sites can then check this token to ensure the user is a human, not a bot.
These tokens are encrypted, so that nobody can disclose the user’s identity.
Interest-based advertising: FLoC API to Topics API and Protected Audience API
Google designed the Federated Learning of Cohorts (FLoC) API to replace third-party cookies for interest-based advertising. The technology grouped users based on similar interests without revealing individual user data, so that advertisers could show relevant ads to audiences.
However, the initial proposal did not last because of the potential to employ fingerprinting techniques that would enable identifying individual users, and Google replaced FLoC with the Topics API.
The Topics API builds upon the principles of FLoC. With the Topics API, a user’s browser determines a handful of topics representing their top interests for a given week based on their browsing history.
When the user visits a participating site, the Topics API shares a limited number of topics (typically three) with the site and its advertising partners. The technology doesn’t reveal individual user data, so advertisers can target users based on aggregated interests without compromising user privacy.
Both technologies, FLoC and Topics API, use on-device processing and local data storage to reduce reliance on external servers and third-party tracking mechanisms.
TURTLEDOVE is an acronym for “Two Uncorrelated Requests, Then Locally-Executed Decision on Victory”, the technology is an API for delivering ads within the browser. The critical goals of TURTLEDOVE include:
-
giving users more control over their data,
-
limiting the data shared with advertisers,
-
reducing the tracking of individuals across websites.
First, the FLEDGE API (First Locally-Executed Decision over Groups Experiment) replaced the TURTLEDOVE API. But then, FLEDGE turned into the Protected Audience API (PAAPI).
The Protected Audience API introduces on-device auctions, where the browser selects relevant ads based on the user’s recorded interests. Advertisers bid on displaying ads without knowing specific user data.
The API focuses on remarketing. Advertisers who have previously interacted with the user inform the user’s browser about their plan to display ads. They can share details about the specific ads they want the user to see and the amount they’re willing to pay for each view. When the user visits a website with ad slots, a browser algorithm decides which ad to potentially show.
The Protected Audience API serves ads based on users’ interests without accessing their identity or visited pages. PETs that PAAPI leverages include on-device processing, local storage, and anonymisation (e.g. k-anonymity).
The Attribution Reporting API offers a fresh approach to measuring ad conversions while maintaining user privacy.
The API empowers advertisers and AdTech providers to measure conversions in various scenarios, including ad clicks and views in third-party iframes or first-party contexts. It achieves this through two types of reports: event-level and summary reports.
-
Event-level reports connect ad interactions with conversion data while maintaining privacy. Delay and noise are incorporated into the reports, preventing linking user identities across various sites. Event-level reports join limited conversion-side data to ad-side identifiers, preventing detailed user tracking. These reports help optimise advertising processes and detect ad fraud.
-
Summary reports offer more comprehensive conversion data without being linked to a specific ad event. They cater to reporting needs, providing insights into the return on investment (ROI) and other essential metrics. The reports are encrypted and sent to AdTech servers.
The Attribution Reporting API requires explicit permission for its usage, ensuring the solution’s security. With this policy, untrusted frames cannot register sources or triggers without authorisation.
Privacy is a vital feature of this API. Unlike third-party cookies that track user activity across sites, the Attribution Reporting API offers insights into conversions without detailed tracking. The information linked across sites is minimal and only required for conversion measurement.
Both report types come with additional privacy protections, such as rate limitations.
Cross-site tracking prevention: First-Party Sets, Shared Storage API, CHIPS, Fenced Frames API, Federated Credential Management
First-Party Sets let a group of related websites act as a single first-party entity, which allows sites in the same set to share information while respecting user privacy boundaries.
The Shared Storage API allows websites with a first-party relationship to share data in a more controlled and secure way, ensuring that only related sites can access shared data while preventing cross-site tracking and unauthorised access.
CHIPS (Cookies Having Independent Partitioned State) intends to enhance user privacy by allowing a website to request specific information from another site, promoting collaboration between websites while minimising the need to expose unnecessary user data.
The Fenced Frames API enhances privacy by allowing iframes within a page to be isolated from each other, preventing cross-frame tracking and reducing the risk of information leakage between different parts of a webpage.
Federated Credential Management allows websites to authenticate users using their existing credentials from another site without sharing the actual login details, enhancing security while reducing the need to expose personal information.
Covert tracking prevention: User-Agent Client Hints, User-Agent Reduction, DNS-over-HTTPS, IP Protection, Privacy Budget, Storage Partitioning, Network State Partitioning, Bounce Tracking Mitigations
The Client Hints API enables websites to request specific information from the browser directly, reducing reliance on the User-Agent string vulnerable to passive fingerprinting. This approach gives users more control over the information they share.
User-Agent Reduction is the effort to minimise the identifying information shared in the User-Agent string, which frauds may use for passive fingerprinting.
DNS-over-HTTPS encrypts DNS queries and responses by encoding them within HTTPS messages. With this protocol, attackers can’t observe which sites a user visits or redirect the user to phishing websites.
IP Protection will hide users’ IP addresses from third parties that could be using IPs to track users across sites.
The Privacy Budget limits fingerprinting. The purpose of the Privacy Budget is to prevent websites from accumulating sufficient data to identify individual users uniquely.
Storage Partitioning isolates specific web APIs used for storage or communication when embedded services access them on a website, particularly within the third-party context.
Network State Partitioning is a concept in web browsers that divides a browser’s network resources — such as connections, DNS cache, and alternative service data — into distinct partitions. Its goal is to prevent sharing these resources across different first-party contexts like websites or web applications.
Bounce tracking mitigations are measures put in place to minimise or eliminate the effectiveness of bounce-tracking techniques, i.e. a technique that allows a third-party site to store a cookie even when third-party cookies are blocked.
Fully Homomorphic Encryption (FHE) Transpiler
Fully Homomorphic Encryption (FHE) is a cryptographic technique that enables computations on encrypted data without the need to decrypt it first. It allows for data to remain encrypted throughout the computation process, therefore preserving privacy and security.
FHE has various potential use cases, including:
-
Secure cloud computing
Users can perform computations on their encrypted data in the cloud without revealing the actual data to the cloud provider.
-
Privacy-preserving machine learning
Machine learning models can be trained on encrypted data, ensuring that the raw data remains private.
-
Secure outsourcing
Organisations can outsource data processing tasks without exposing sensitive information.
-
Confidential data sharing
Multiple parties can collaborate on encrypted data without revealing individual contributions.
How Are Google, Meta, Apple, Amazon, and Microsoft Adopting Privacy-Enhancing Technologies?
Thank you for reading our article on how Google uses privacy-enhancing technologies. We trust it has expanded your knowledge of secure solutions applied by the search giant in its advertising systems.
This is the second article in our series on tech giants adopting PETs. In the first part, we covered how cyber giants adopt PETs to meet regulatory requirements, mitigate data breach risks, and securely monetise user data.
If you have any questions or comments, reach out to us and we’ll get back to you in no time!

